Drag and Drop
Drag and drop the methods supported by the aaa authorization command from me left onto me correct descriptions on the right.
Select and Place:
Drag and Drop
Drag and drop the methods supported by the aaa authorization command from me left onto me correct descriptions on the right.
Select and Place:

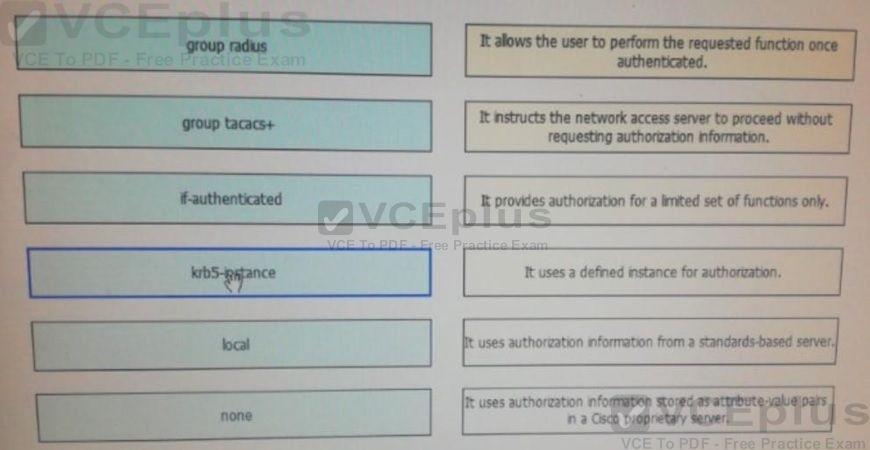
group radius 5
groups tacacs+ 6
if-authenticated 1
krb5-instance 4
local 3
none 2
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_usr_aaa/configuration/xe-3s/sec-usr-aaa-xe-3s-book/sec-cfg-authorizatn.html
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_usr_aaa/configuration/xe-3s/sec-usr-aaa-xe-3s-book/sec-cfg-authentifcn.html
group radius 5
groups tacacs+ 6
if-authenticated 1
krb5-instance 4
local 3
none 2
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_usr_aaa/configuration/xe-3s/sec-usr-aaa-xe-3s-book/sec-cfg-authorizatn.html
AAA Authorization Methods
AAA supports five different methods of authorization:
TACACS+—The network access server exchanges authorization information with the TACACS+ security daemon. TACACS+ authorization defines specific rights for users by associating attribute-value pairs, which are stored in a database on the TACACS+ security server, with the appropriate user.
If-Authenticated—The user is allowed to access the requested function provided the user has been authenticated successfully.
None—The network access server does not request authorization information; authorization is not performed over this line/interface.
Local—The router or access server consults its local database, as defined by the username command, for example, to authorize specific rights for users. Only a limited set of functions can be controlled via the local database.
RADIUS—The network access server requests authorization information from the RADIUS security server. RADIUS authorization defines specific rights for users by associating attributes, which are stored in a database on the RADIUS server, with the appropriate user.
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_usr_aaa/configuration/xe-3s/sec-usr-aaa-xe-3s-book/sec-cfg-authentifcn.html
krb5
Uses Kerberos 5 for authentication (can only be used for PAP authentication).