Home » Cisco » 300-115 » Lab Simulation – AAAdot1x
Lab Simulation – AAAdot1x
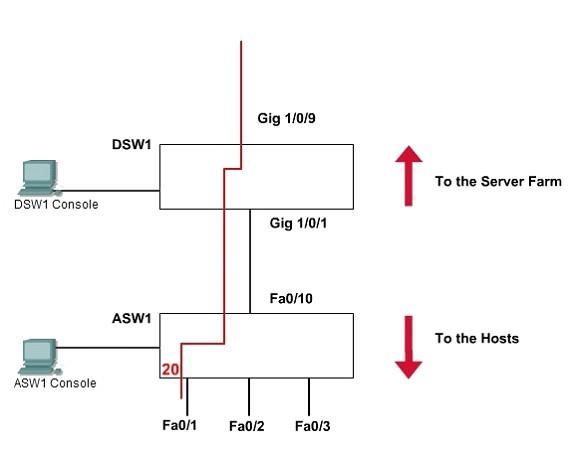
SWITCH.com is an IT company that has an existing enterprise network comprised of two layer 2 only switches; DSW1 and ASW1. The topology diagram indicates their layer 2 mapping. VLAN 20 is a new VLAN that will be used to provide the shipping personnel access to the server.
Corporate polices do not allow layer 3 functionality to be enabled on the switches.
For security reasons, it is necessary to restrict access to VLAN 20 in the following manner:
– Users connecting to VLAN 20 via portfO/1 on ASW1 must be authenticated before they are given access to the network.
Authentication is to be done via a Radius server:
– Radius server host: 172.120.40.46
– Radius key: rad123
– Authentication should be implemented as close to the host as possible.
– Devices on VLAN 20 are restricted to the subnet of 172.120.40.0/24.
– Packets from devices in the subnet of 172.120.40.0/24 should be allowed on VLAN 20.
– Packets from devices in any other address range should be dropped on VLAN 20.
– Filtering should be implemented as close to the serverfarm as possible.
The Radius server and application servers will be installed at a future date. You have been tasked with implementing the above access control as a pre-condition to installing the servers. You must use the available IOS switch features.
Answer:
1. Verification of Pre-configuration:
a. Check that the denoted vlan [vlan20] is created in both switches and ports [fa0/1 of ASW1] are assigned.
b. Take down the radius-server ip [172.120.39.46] and the key [rad123].
c. Take down the IP range [172.120.40.0/24] to be allowed the given vlan [vlan20]
2. Configure the Port based authentication on ASW1:
Enable AAA on the switch:
ASW1(config)# aaa new-model
The new-model keyword refers to the use of method lists, by which authentication methods and sources can be grouped or organized. Define the server along with its secret shared password:
ASW1(config)# radius-server host 172.120.39.46 key rad123
ASW1(config)# aaa authentication dot1x default group radius
This command causes the RADIUS server defined on the switch to be used for 802.1x authentication.
Enable 802.1x on the switch:
ASW1(config)# dot1x system-auth-control
Configure Fa0/1 to use 802.1x:
ASW1(config)# interface fastEthernet 0/1
ASW1(config-if)# switchport mode access
ASW1(config-if)# dot1x port-control auto
Notice that the word “auto” will force connected PC to authenticate through the 802.1x exchange.
ASW1(config-if)# exit
ASW1# copy running-config startup-config
3. Filter the traffic and create vlan access-map to restrict the traffic only for a range on DSW1
Define an access-list:
DSW1(config)# ip access-list standard 10 (syntax: ip access-list {standard | extended} acl-name)
DSW1(config-ext-nacl)# permit 172.120.40.0 0.0.0.255
DSW1(config-ext-nacl)# exit
Define an access-map which uses the access-list above:
DSW1(config)# vlan access-map MYACCMAP 10 (syntax: vlan access-map map_name [0-65535] )
DSW1(config-access-map)# match ip address 10 (syntax: match ip address {acl_number | acl_name})
DSW1(config-access-map)# action forward
DSW1(config-access-map)# exit
DSW1(config)# vlan access-map MYACCMAP 20
DSW1(config-access-map)# action drop (drop other networks)
DSW1(config-access-map)# exit
Apply a vlan-map into a vlan:
DSW1(config)# vlan filter MYACCMAP vlan-list 20 (syntax: vlan filter mapname vlan-list list)
DSW1# copy running-config startup-config
4. Note:
It is not possible to verify the configuration in this lab. All we have do the correct configurations. Most of the exam takers report that “ copy running-config startup-config” is not working. It does not a matter.
Do not try unwanted/wrong commands in the consoles. They are not real switches.



