An organization has established the following controls matrix:
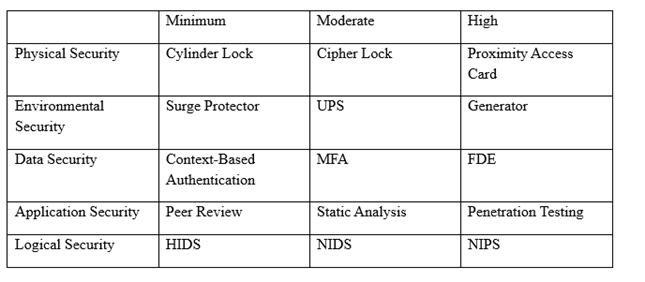
The following control sets have been defined by the organization and are applied in aggregate fashion:
▪ Systems containing PII are protected with the minimum control set.
▪ Systems containing medical data are protected at the moderate level.
▪ Systems containing cardholder data are protected at the high level.
The organization is preparing to deploy a system that protects the confidentially of a database containing PII and medical data from clients. Based on the controls classification, which of the following controls would BEST meet these requirements?
A. Proximity card access to the server room, context-based authentication, UPS, and full-disk encryption for the database server.
B. Cipher lock on the server room door, FDE, surge protector, and static analysis of all application code.
C. Peer review of all application changes, static analysis of application code, UPS, and penetration testing of the complete system.
D. Intrusion detection capabilities, network-based IPS, generator, and context-based authentication.
How to PASS CAS-004 in First Attempt?FULL Printable PDF and Software. VALID exam to help you PASS. |
 |


I’d go with D because it includes intrusion detection and network IPS which both provide more real-world protection than the other controls do.
Maybe: B. Cipher lock on the server room door, FDE, surge protector, and static analysis of all application code ?
This is an awful and completely unfair question. None of the options meet the specified standards. However, I think it can be argued that B is the least wrong.
They are trying to protect confidentiality not integrity or availability. Since the database contains PII and medical data, the protection levels should be moderate or higher.
A. Proximity card access to the server room, context-based authentication, UPS, and full-disk encryption for the database server.
For data security category: has both context-based security, and FDE. Has no logical security at all. No application security. Fails on, at least, two counts.
B. Cipher lock on the server room door, FDE, surge protector, and static analysis of all application code.
Surge protector is minimum security. But we are only looking at confidentiality, not data integrity, or availability. No logical protection at all. Fails on, at least, one count. Since this fails less than the others, I suppose this is the best answer.
C. Peer review of all application changes, static analysis of application code, UPS, and penetration testing of the complete system.
Again, no logical protection. Also no physical security. Fails on, at least, two counts.
D. Intrusion detection capabilities, network-based IPS, generator, and context-based authentication.
Context-based authentication is minimum protection. Intrusion detection capabilities is not listed. No application security. This is the only one with any logical protection. Fails on, at least, two counts.
A also had FDE for the database, and you said UPS, it has UPS too, it’s A…
Ah man, I totally get what you are saying. It’s A.
I would go with B mainly because we are talking about database containing PII and medical data from clients. Data is priority and we would use a Full-disk encryption (FDE). Cipher lock is still under MEDIUM, I would prefer a UPS but they fail just as much as a Surge but Availability is not the concern here.
The answer is A!
the company wants to secure their database and techniques such as full-disk encryption for the database server is important due to the reason the database contains medical and PII data. D – IDS will only detect the data and access without permission.
B also has FDE.
Yes, for data security category: ‘A’ has both context-based security, and FDE.
But ‘A’ has no logical security at all. No application security. Fails on, at least, two counts.