A security engineer successfully exploits an application during a penetration test. As proof of the exploit, the security engineer takes screenshots of how data was compromised in the application. Given the information below from the screenshot.
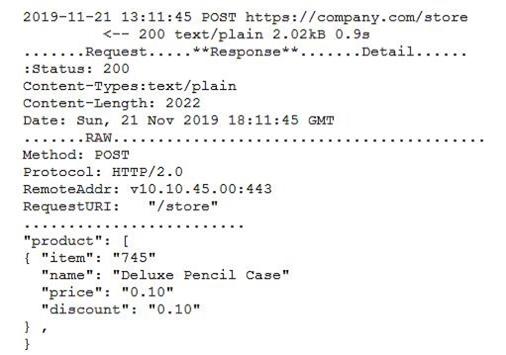
Which of the following tools was MOST likely used to exploit the application?
A. The engineer captured the data with a protocol analyzer, and then utilized Python to edit the data
B. The engineer queried the server and edited the data using an HTTP proxy interceptor
C. The engineer used a cross-site script sent via curl to edit the data
D. The engineer captured the HTTP headers, and then replaced the JSON data with a banner-grabbing tool
How to PASS CAS-004 in First Attempt?FULL Printable PDF and Software. VALID exam to help you PASS. |
 |


Just to make sure I understand: all of these mean the same, correct?
MITM Proxy
HTTP Proxy Interceptor
HTTP Interceptor
HTTP interception (and HTTPS “Break and Inspect” interception) counts as MITM, whether sanctioned or an attack, but MITM (Man-in-the-Middle) is a broader category.
agree with B.
B.