An information security officer is responsible for one secure network and one office network. Recent intelligence suggests there is an opportunity for attackers to gain access to the secure network due to similar login credentials across networks. To determine the users who should change their information, the information security officer uses a tool to scan a file with hashed values on both networks and receives the following data:
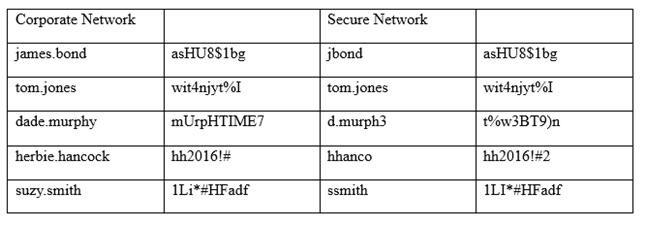
Which of the following tools was used to gather this information from the hashed values in the file?
A. Vulnerability scanner
B. Fuzzer
C. MD5 generator
D. Password cracker
E. Protocol analyzer
How to PASS CAS-004 in First Attempt?FULL Printable PDF and Software. VALID exam to help you PASS. |
 |


D
“Which of the following tools was used to gather this information from the hashed values in the file?”
A. No, just how even. Unless the scanner executes mimikatz or something… not a thing AFAIK.
B. No, don’t look here.
C. No… just can’t even with this answer. I mean these are not even MD5 hashes… so…
D. Yes, we gained passwords from hashed values in the file by cracking them.
E. Eh, possibly this data was harvested from the wire in the form of a PCAP and if they were sent in the clear, sure, but it wouldn’t be the data here is clear text passwords.
I agree should be D
not sure on this one either,
key here is: ” information security officer uses a tool to scan a file with hashed values on both networks and receives the following data”
what tool could this be?
Its password cracker.
There is nothing to Fuzz here
We arent using a scanner since scanners arent typically used for password cracking
MD5 generator is that….a generates Md5. If it was a Md5 cracker then I would go with that answer. But its not
Protocol analyer…..thats a no
Password cracker. Tools like jack the ripper or rainbow tables come to mind.
The hashes are already in the file? Maybe E, but that would be a weird way for an ISO to go about getting this information….