Refer to the exhibit. If the traffic flowing from network 192.168.254.0 to 172.16.250.0 is unencrypted, which two actions must you take to enable encryption? (Choose two).
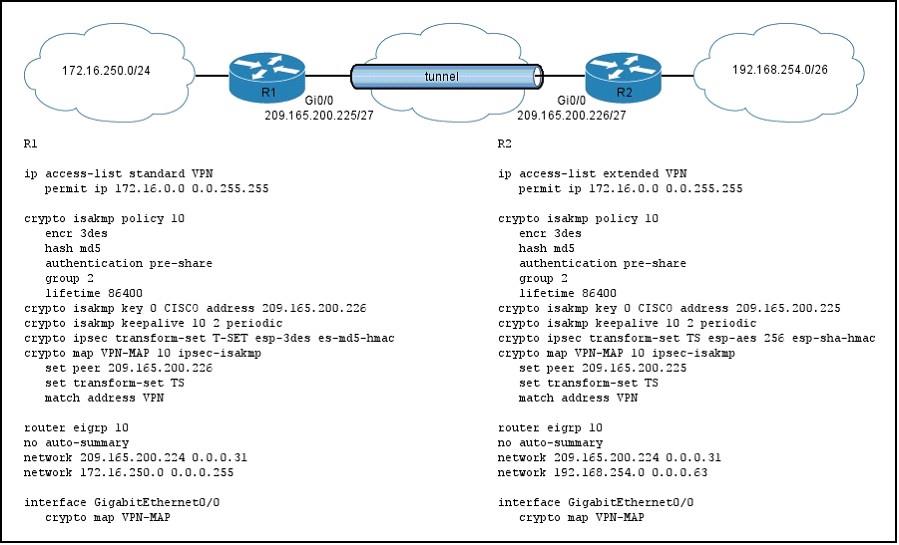
A. Configure the transform-set on R2 to match the configuration on R1.
B. Configure the crypto map on R2 to include the correct subnet.
C. Configure the ISAKMP policy names to match on R1 and R2.
D. Configure the crypto map names to match on R1 and R2.
E. Configure the Diffie-Hellman keys used in the ISAKMP policies to be different on R1 and R2.

