Click the Exhibit button.
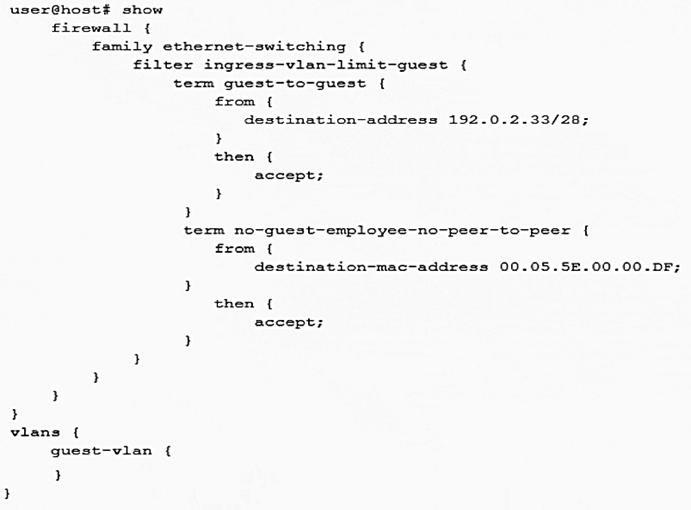
A recent security audit indicates that peer-to-peer applications are allowed on the guest VLAN and employees may have been using the guest VLAN for this purpose. You deploy the configuration shown in the exhibit, but it does not stop the peer-to-peer traffic.
In this scenario, what must you do to implement the security policy?
A. Implement 802.1X on the guest VLAN
B. Attach the filter to the VLAN
C. Deploy storm control to block unknown unicast traffic
D. Use persistent MAC learning

