DRAG DROP
Your network contains a System Center 2012 Configuration Manager environment.
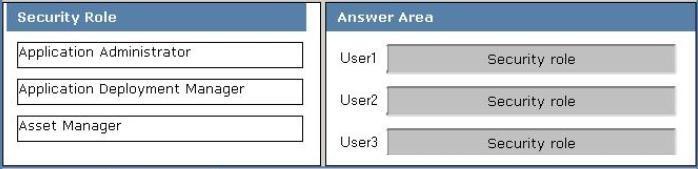
Three users named User1, User2, and User3 will perform the following tasks:
User1 will review software metering data and inventory reports.
User2 will deploy Applications and create alerts.
User3 will create configuration items.
You need to identify which security role must be assigned to which user.
What should you identify?
To answer, drag the appropriate security role to the correct user in the answer area. Each security role may be used once, more than once, or not at all. Additionally, you may need to drag the split bar between panes or scroll to view content.
Select and Place: