Refer to the exhibit Which two effects of this configuration are true? (Choose two)
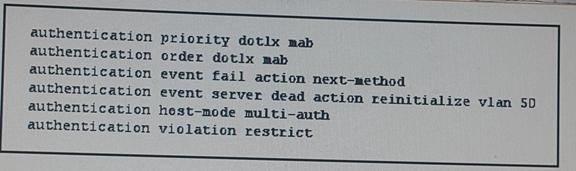
A. If the TACACS+ server is unreachable, the switch places hosts on critical ports in VLAN 50
B. If the authentication priority is changed, the order in which authentication is performed also changes.
C. If multiple hosts have authenticated to the same port, each can be in their own assigned VLAN
D. The port attempts 802.1x authentication first, and then falls back to MAC authentication bypass
E. The device allows multiple authenticated sessions for a single MAC address in the voice domain.
F. The switch periodically sends an EAP-ldentity-Request to the endpoint supplicant


When a port is in multiple-authentication mode, the guest VLAN and the authentication-failed VLAN features do not activate.
After a VLAN is assigned to a host on the port, subsequent hosts must have matching VLAN information or be denied access to the port.
the term “EAP-ldentity-Request” does not exist. This is a tricky answer. However the term ” EAP-Request-Identity” does exist. This is why i would be discarding answer F and will be selecting A.
So right answers would be: A and D.
A is not correct as 802.1x only supported with RADIUS and not TACACS
I agree with Lblc with “A” NOT being correct, besides the fact that they should’ve said “Radius”. One more reason to justify this is because the wording is wrong as well. they should’ve said “…places hosts on ports in CRITICAL VLAN 50” and not “places hosts on CRITICAL PORTS in VLAN 50”. The VLAN is the one that should be named “critical” and not the port.
https://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Security/TrustSec_1-99/Dot1X_Deployment/Dot1x_Dep_Guide.html
•Multi-auth host mode
If the port is configured for multi-auth mode, multiple endpoints can be authenticated in the data VLAN. Each new MAC address that appears on the port is separately authenticated. Multi-auth can be used for bridged virtual environments or to support hubs.
An 802.1X authentication can be initiated by either the switch or the supplicant. From the perspective of the switch, the authentication session begins when the switch detects a link up on a port. The switch initiates authentication by sending an EAP-Request-Identity message to the supplicant. If the switch does not receive a response, the switch retransmits the request at periodic intervals.
The supplicant can initiate authentication by sending an EAPoL-Start frame. The EAPoL-Start message enables supplicants to speed up the authenticate process without waiting for the next periodic EAP-Request-Identity from the switch. EAPoL-Start messages are required in situations where the supplicant is not ready to process an EAP-Request from the switch (for example, because the operating system is still booting); or where there is no physical link state change on the switch (for example, because the supplicant is indirectly connected via an IP phone or hub).