Drag and Drop
A security analyst suspects that a workstation may be beaconing to a command and control server. You must inspect the logs from the company’s web proxy server and the firewall to determine the best course of action to take in order to neutralize the threat with minimum impact to the organization.
Instructions:
If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
A. Answer below
CS0-002: CompTIA CySA+ ExamFULL Printable PDF and Software. VALID exam to help you PASS. |
 |

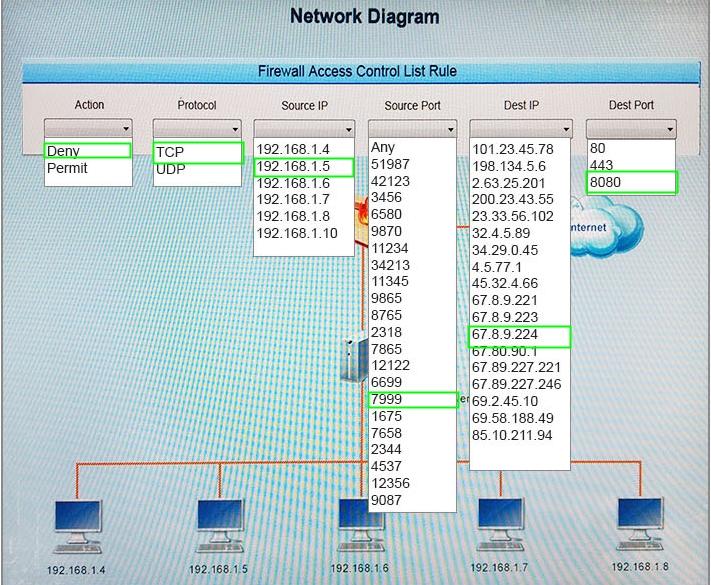
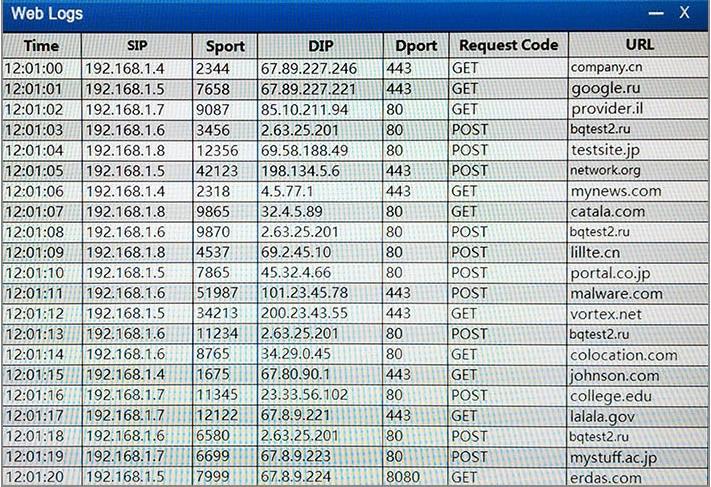
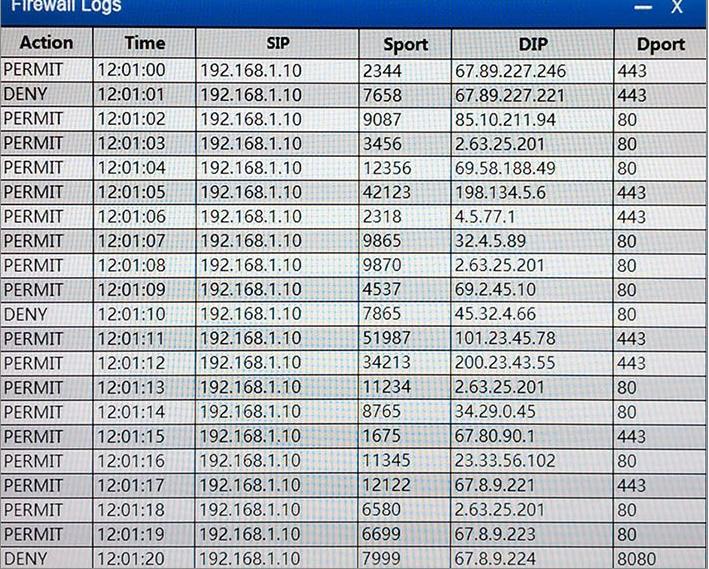

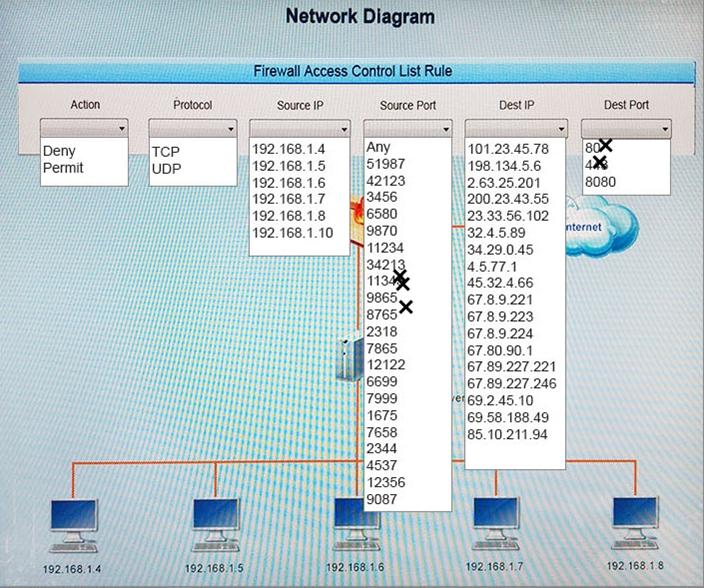
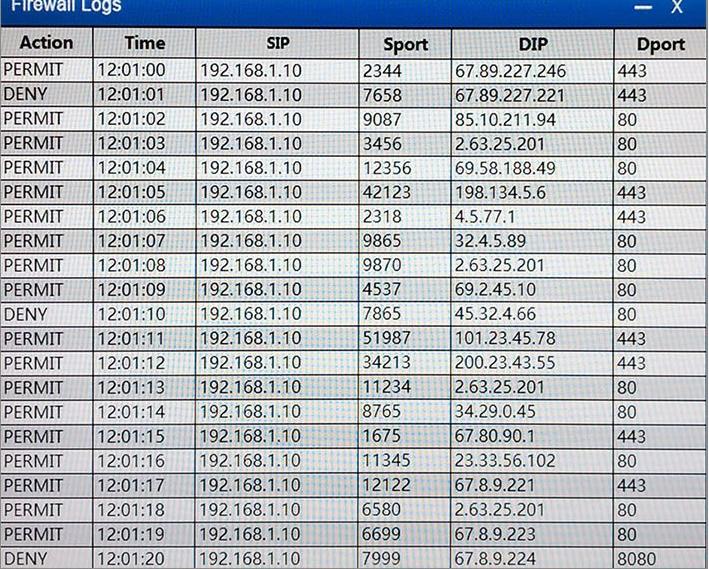
If you are blocking from the firewall the IP should be 192.168.1.10
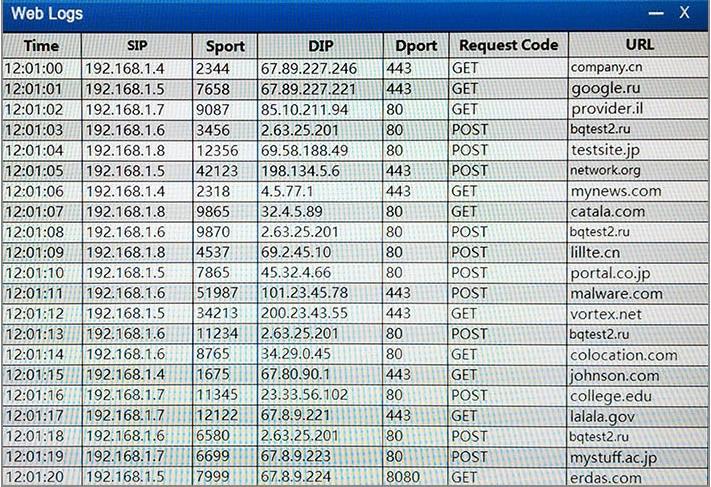
The reason you are blocking 1.5 is that the question asks about beaconing, because of bqtest.ru is showing clear signs of beaconing appering every several minutes in the log.
Deny, TCP, 192.168.1.6, Any, 2.63.25.201, 80
It does not seem to be the correct answer. Can someone explain?
is it not: DENY, TCP, 192.168.1.6, ANY,2.63.25.201,80 ?
Can someone please explain why X.5 would be the one to block going out to erdas.com. Is it because its the only one going out of port 8080?
Why not block ip X.6 going out to malware.com?