A security analyst is reviewing the following log after enabling key-based authentication.
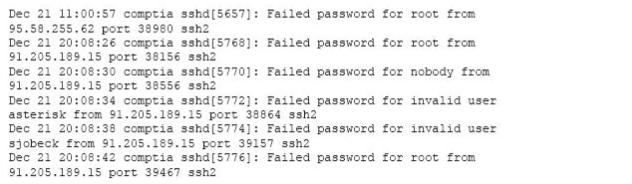
Given the above information, which of the following steps should be performed NEXT to secure the system?
A. Disable anonymous SSH logins.
B. Disable password authentication for SSH.
C. Disable SSHv1.
D. Disable remote root SSH logins.
CS0-002: CompTIA CySA+ ExamFULL Printable PDF and Software. VALID exam to help you PASS. |
 |


i think it should be D