A cybersecurity consultant is reviewing the following output from a vulnerability scan against a newly installed MS SQL Server 2012 that is slated to go into production in one week:
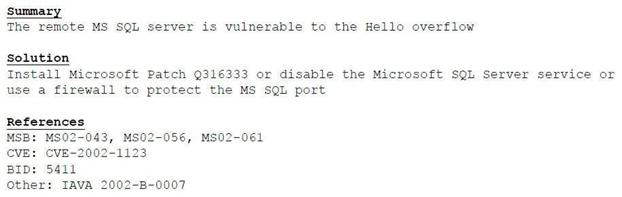
Based on the above information, which of the following should the system administrator do? (Select TWO).
A. Verify the vulnerability using penetration testing tools or proof-of-concept exploits.
B. Review the references to determine if the vulnerability can be remotely exploited.
C. Mark the result as a false positive so it will show in subsequent scans.
D. Configure a network-based ACL at the perimeter firewall to protect the MS SQL port.
E. Implement the proposed solution by installing Microsoft patch Q316333.
CS0-002: CompTIA CySA+ ExamFULL Printable PDF and Software. VALID exam to help you PASS. |
 |


If you choose D you will block the service itself : I go with B and E
Hello dead cow cult:
The SQL server should not be accessible directly through the perimeter firewall. If you want access from outside you should consider other solutions like: VPN, JumpBox or other services to drop inside the DMZ. Actually D should never be an option, because the SQL should not be accessible through the perimeter.
In regards to your B answer: the fact that you used a Vulnerability tool and have a report, you already have an external reference that the vulnerability can be indeed exploited. If you would like to prove a point, then go with A. But in this particular case, according to CompTIA logic, the right way to go is D and E.