Scenario: A Citrix Architect needs to design a new XenApp and XenDesktop environment.
The architect has identified the User Layer requirements, as shown in the Exhibit. Click the Exhibit button to view the requirements.
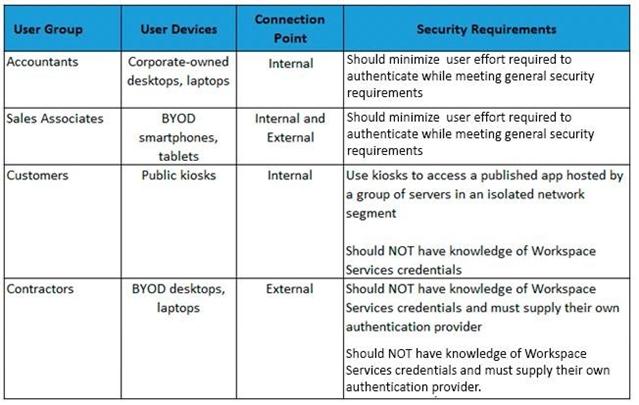
Additionally, management at the organization has identified the following general Access Layer requirements:
A multi-factor authentication method is required for any connections to the XenApp and XenDesktop environment originating from outside the corporate network. External connections must be authenticated by a NetScaler Gateway virtual server located in a DMZ network. Internal connection traffic should NOT leave the internal corporate network.
Which Access Layer feature should the architect configure to meet the security requirements of the Accountants group?
A. Unified Gateway
B. SmartAccess
C. SmartControl
D. NetScaler Double Hop
E. Endpoint analysis scan


I think A is correct
E. Not applicable – When Citrix Gateway installs the Endpoint Analysis plug-in on the user device, the Plug- in scans the user device for the endpoint security
requirements that you configured on Citrix Gateway. The requirements include information, such as the operating system, antivirus, or web browser versions.
Yet another asinine question that is worded very poorly. The only possible answer I can come up with is B smart access as smart access takes place on the delivery controller. All other answers take place on the netscaler which is OUTSIDE the internal network in the DMZ.
The way this is worded it sounds like they don’t want someone working on the inside to browse the internet.
My biggest complaint about the certification game is there’s no way to challenge those who create these tests and dispute correct answers that they think are wrong.
I agree that it is probably E. following authentication, the SF beacon should show they are in the internal network and then bypass the netscaler for connection traffic. Double-Hop just uses a second NS as a proxy for internal traffic. B and C should be out because it doesn’t specify they need apps/desktops filtered.
No sure, maybe B
D is the right answer
I think E is correct. In the access layer best practices Citrix only talks about EPA Scan: https://docs.citrix.com/en-us/xenapp-and-xendesktop/7-15-ltsr/citrix-vdi-best-practices/design/design-userlayer2.html