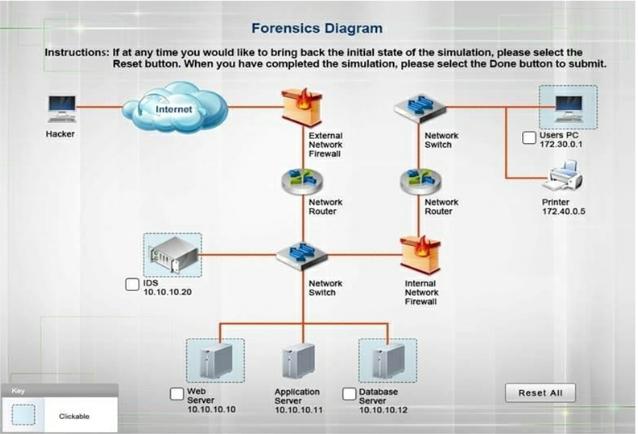
SIMULATION
A security administrator discovers that an attack has been completed against a node on the corporate network. All available logs were collected and stored.
You must review all network logs to discover the scope of the attack, check the box of the node(s) that have been compromised and drag and drop the appropriate actions to complete the incident response on the network. The environment is a critical production environment; perform the LEAST disruptive actions on the network, while still performing the appropriate incid3nt responses.
Instructions: The web server, database server, IDS, and User PC are clickable. Check the box of the node(s) that have been compromised and drag and drop the appropriate actions to complete the incident response on the network. Not all actions may be used, and order is not important. If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit.
Once the simulation is submitted, please select the Next button to continue.
Your Response: type here
A. "See the solution below."


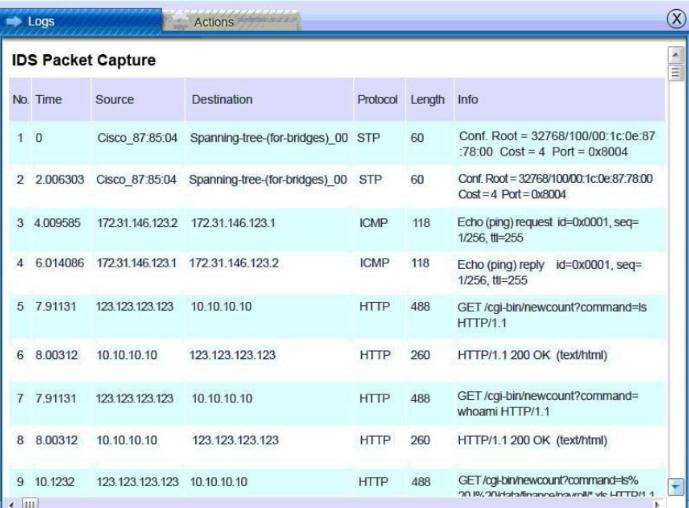
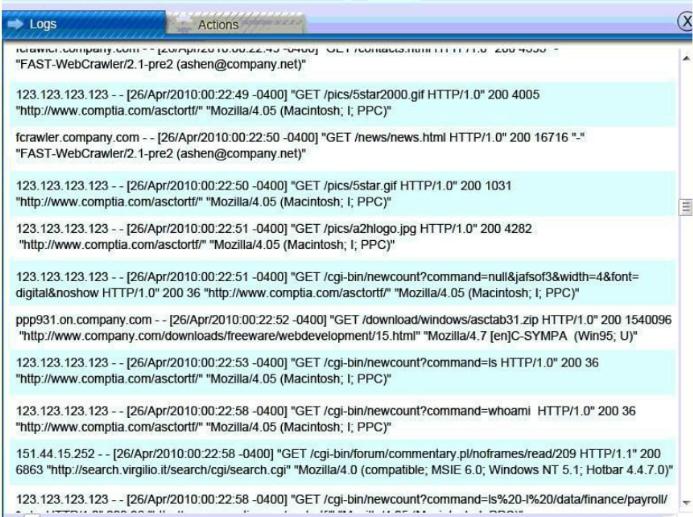

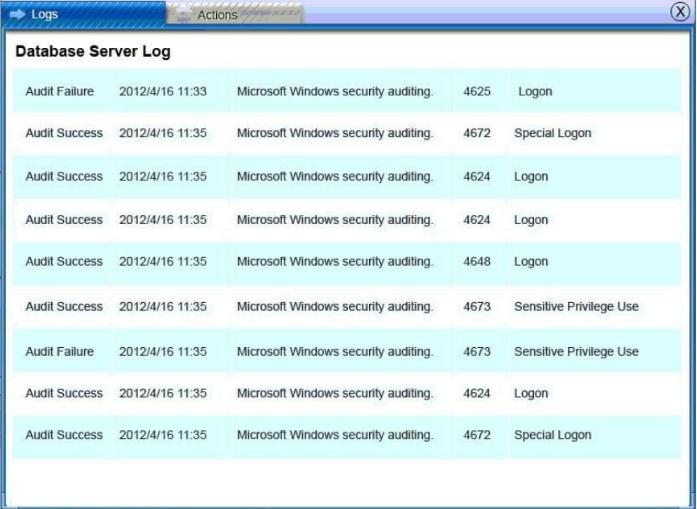



From what we can see of the logs:
IDS Packet Capture log is WireShark format – need to scroll down to see more (not displayed here). Time format is relative to previous displayed packet.
PC’s address 172.30.0.10 is not displayed in current frame – scroll down to find.
External IP 123.123.123.123 to 10.10.10.10 (web server) is displayed at record number 5 with an LS cmd and gets an OK.
https://www.juniper.net/documentation/en_US/idp5.1/topics/example/simple/intrusion-detection-prevention-packet-capture-viewing.html
https://www.wireshark.org/docs/wsug_html_chunked/ChWorkTimeFormatsSection.html
Internet logs: show several interactions between 123.123.123.123 and 10.10.10.10.
“Get” cmd issued to copy *.xls from payroll (10.10.10.12 DB server)?
https://flylib.com/books/en/3.210.1.52/1/
The web server 10.10.10.10 was under attack. It looks like an attacker from 123.123.123.123 has listed (LS) the xls files from /data/finance/payroll (DB server?) and copied (SCP) the file gl-Nov2010.xls to the root directory of their machine. This appears to be a command injection attack.
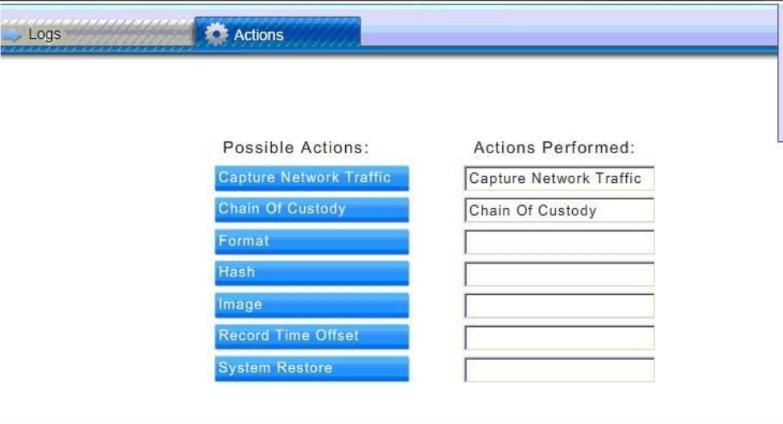
ANSWER: The actions to take are:
Capture Network Traffic: To prove that the network has been breached and data has been stolen.
Chain of Custody: start a chain of custody and document the steps taken to secure physical access to the web server.
Record Time Offset: time offset between the web server and IDS to establish a consistent chronology to the events.
Image the hard drive?
Hash image and hard drive to confirm exact duplicates?